Recent years have seen rapid digital transformation (DX) across companies, while cyberattack techniques continue to grow more sophisticated, exposing many organizations to increasing security threats.
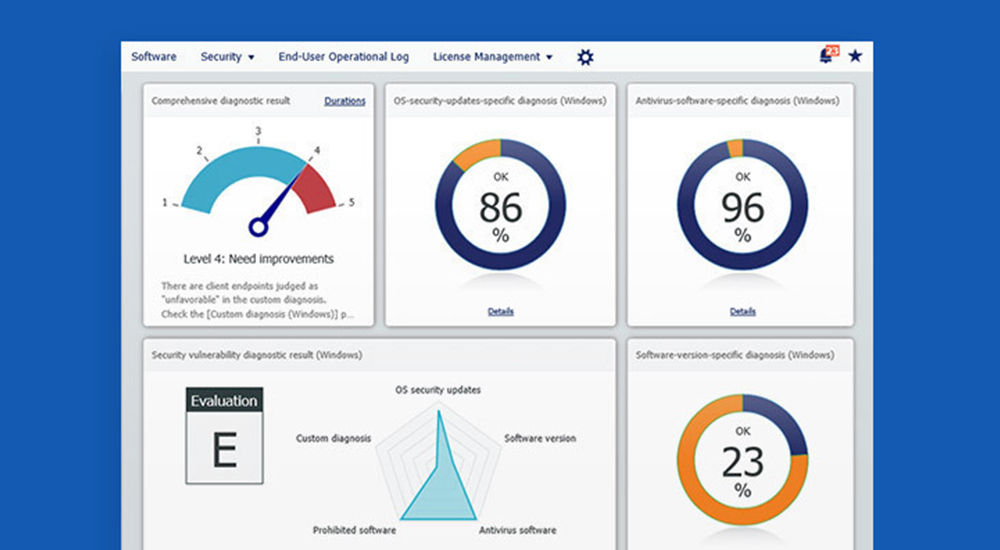
Proactive security measures are essential to protect your company’s information assets and customer trust. Among these, vulnerability assessments are a fundamental and critical undertaking.
Across countries, responses to vulnerabilities are increasingly being codified through guidelines and regulation. In Japan and the U.S., the IPA (Information-technology Promotion Agency, Japan) and NIST (National Institute of Standards and Technology) provide guidelines; in Europe, the NIS2 Directive and the Digital Operational Resilience Act (DORA) mandate organizational measures for critical infrastructure and the financial sector, making such efforts indispensable to operating a business.
This article provides a clear explanation of the basics of vulnerability assessments, why they are necessary, their types, typical costs, and how to choose the right service for your organization.